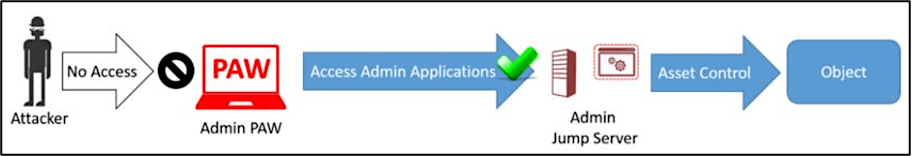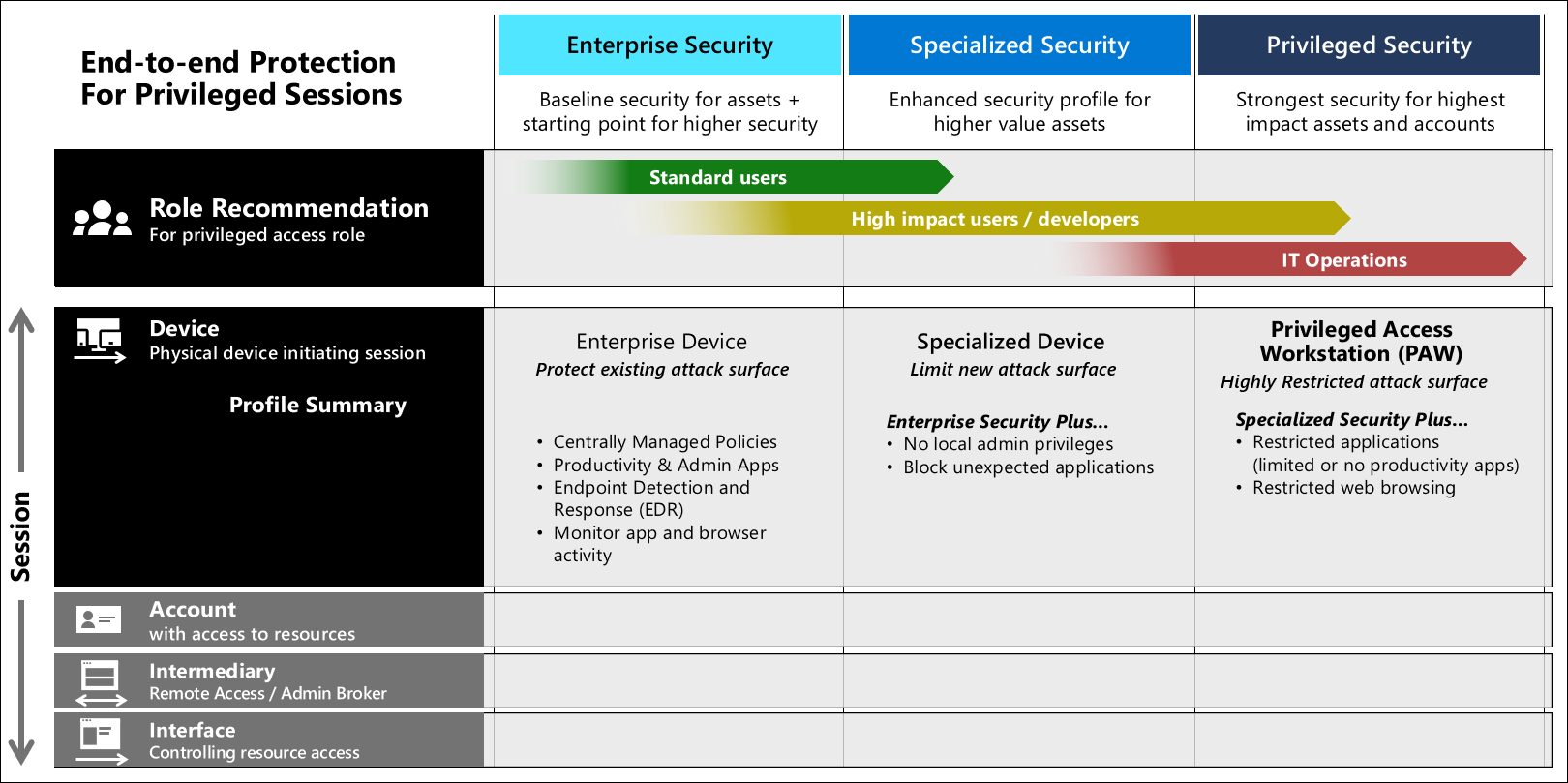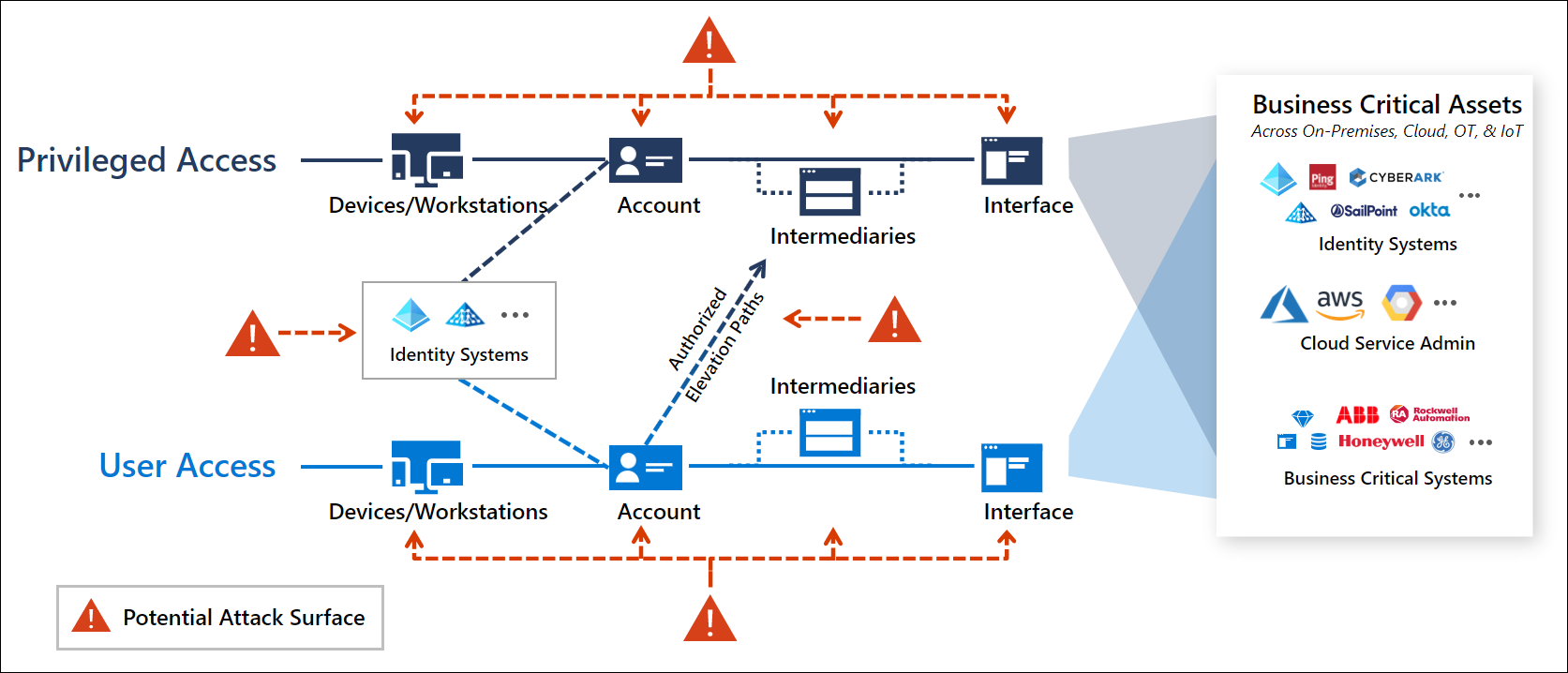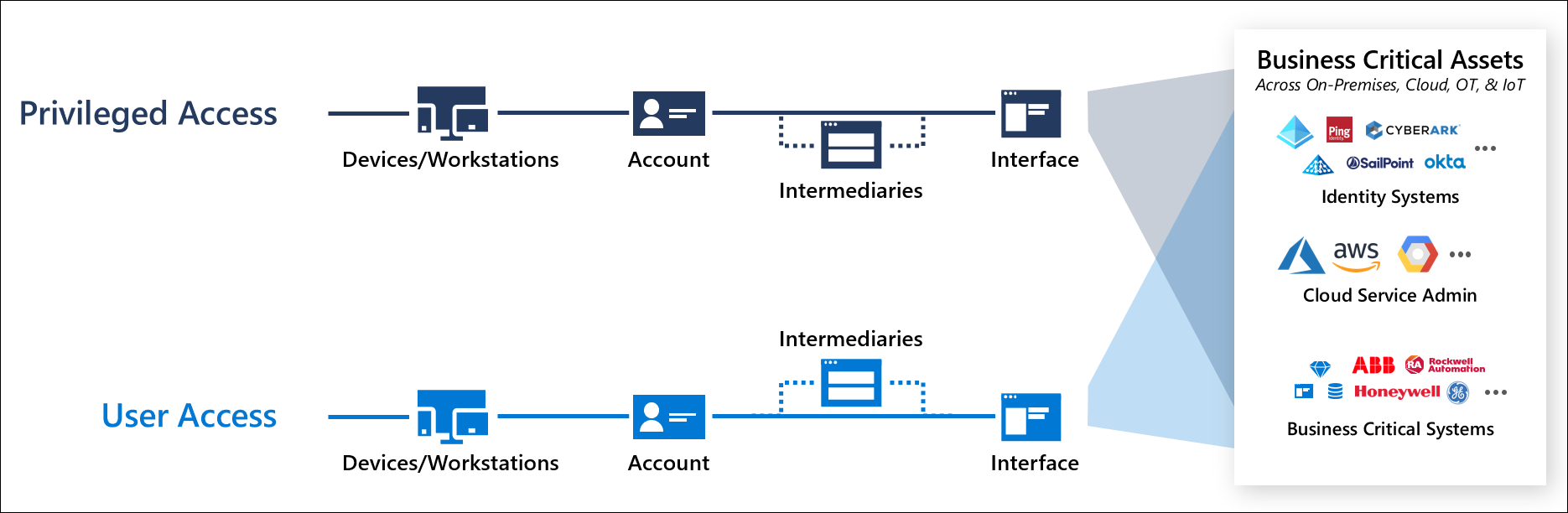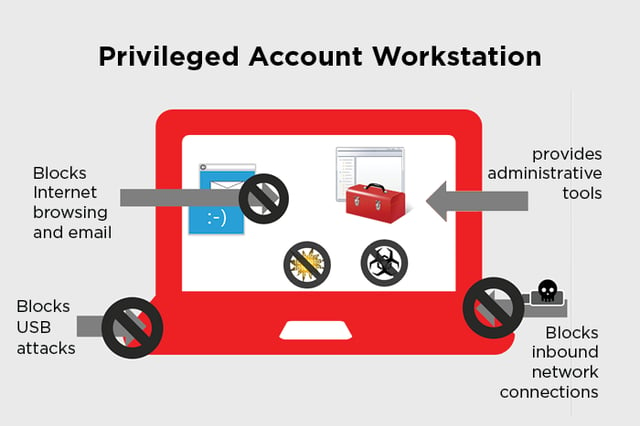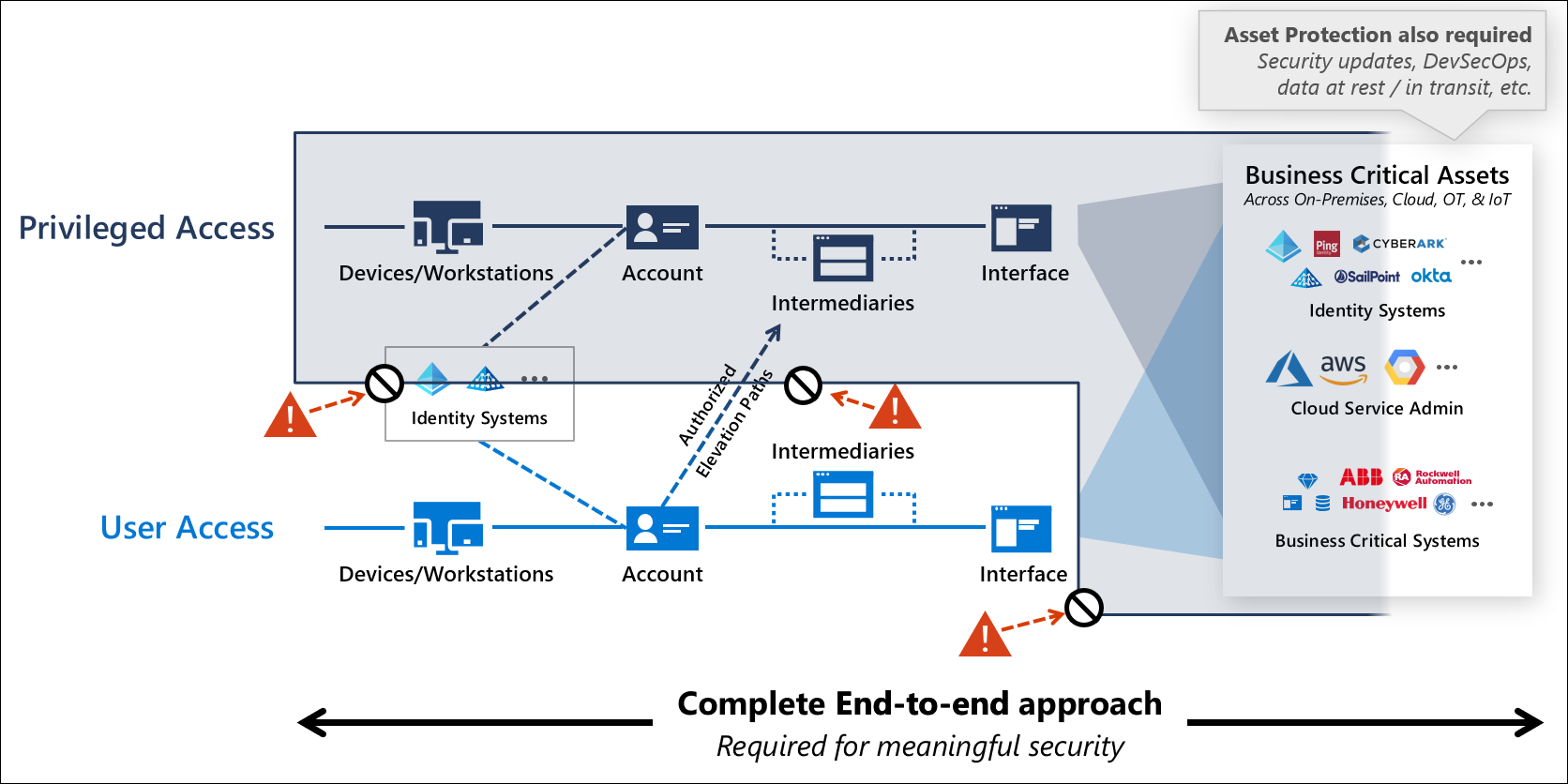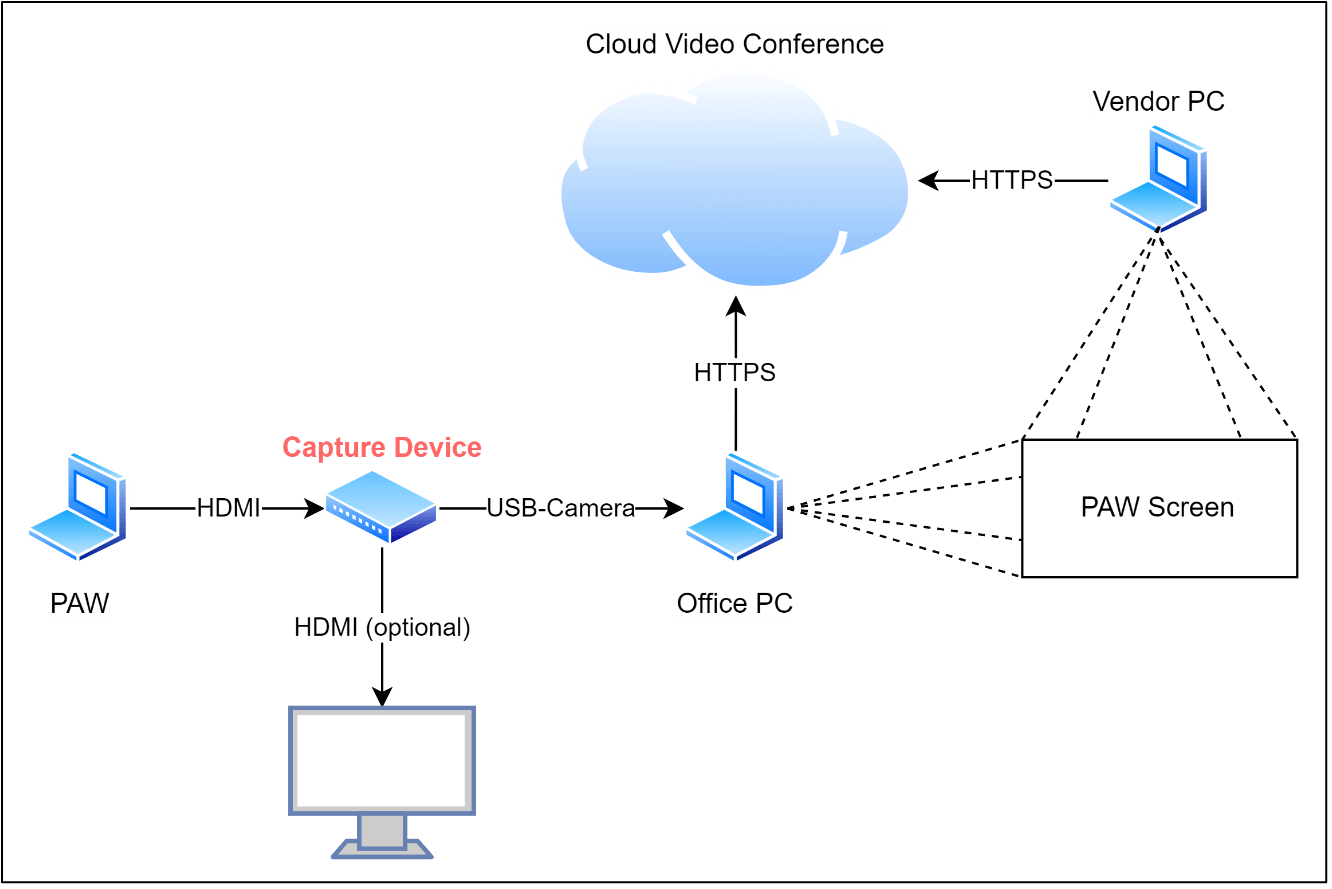
Privileged Access Workstation (PAW) – Deep Dive und praktische Umsetzung - TEAL Technology Consulting GmbH
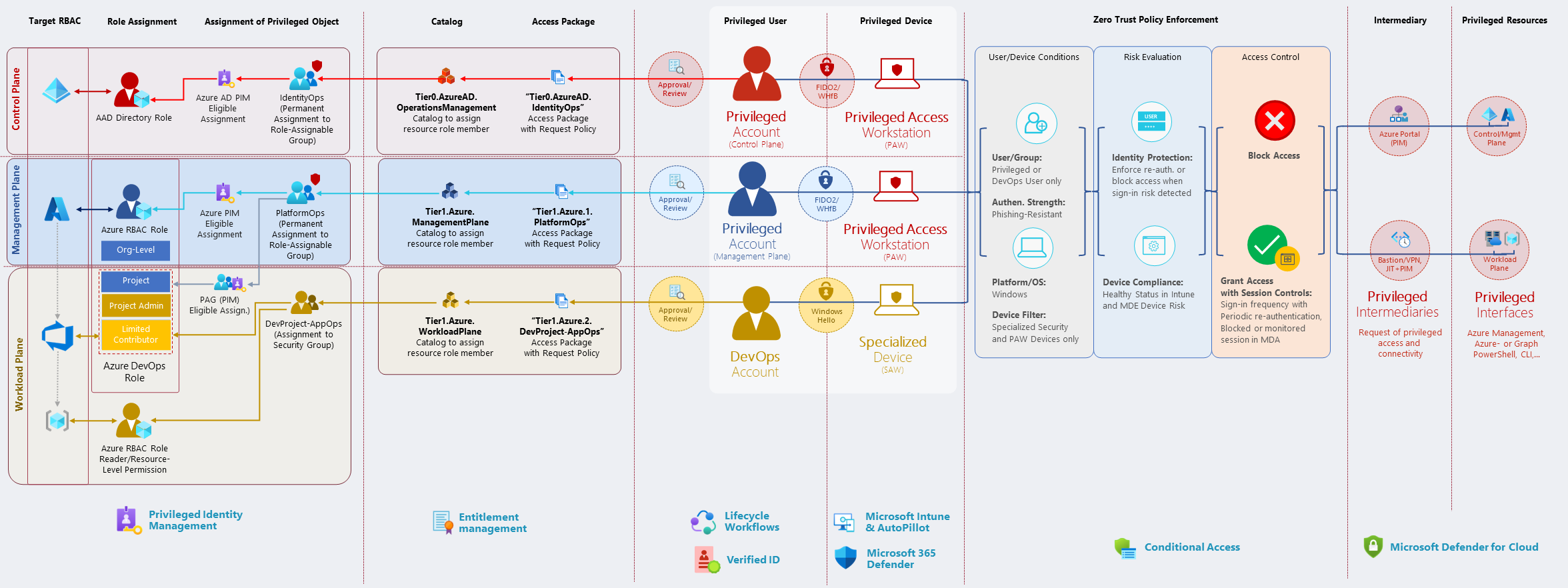
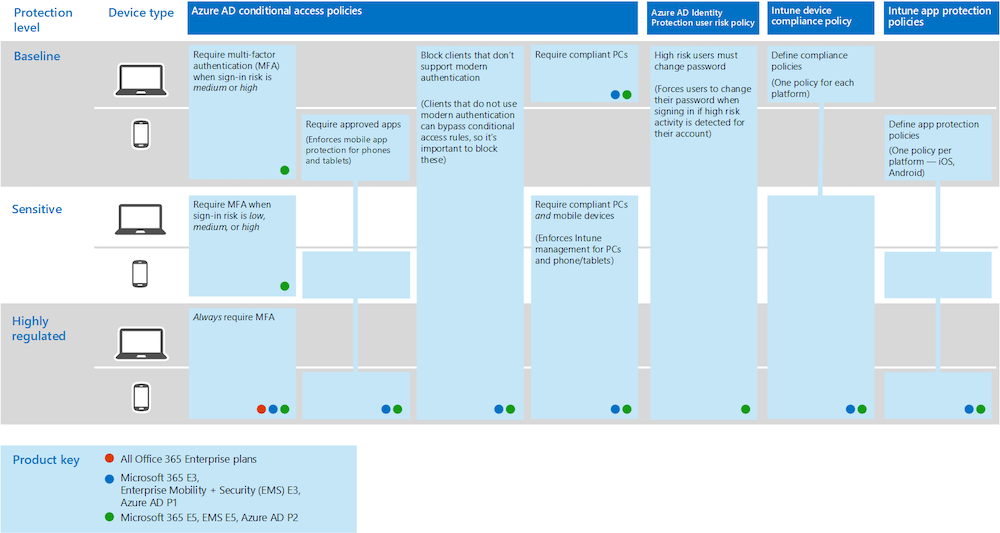
Securing privileged user access with Azure AD Conditional Access and Identity Governance - Thomas Naunheim
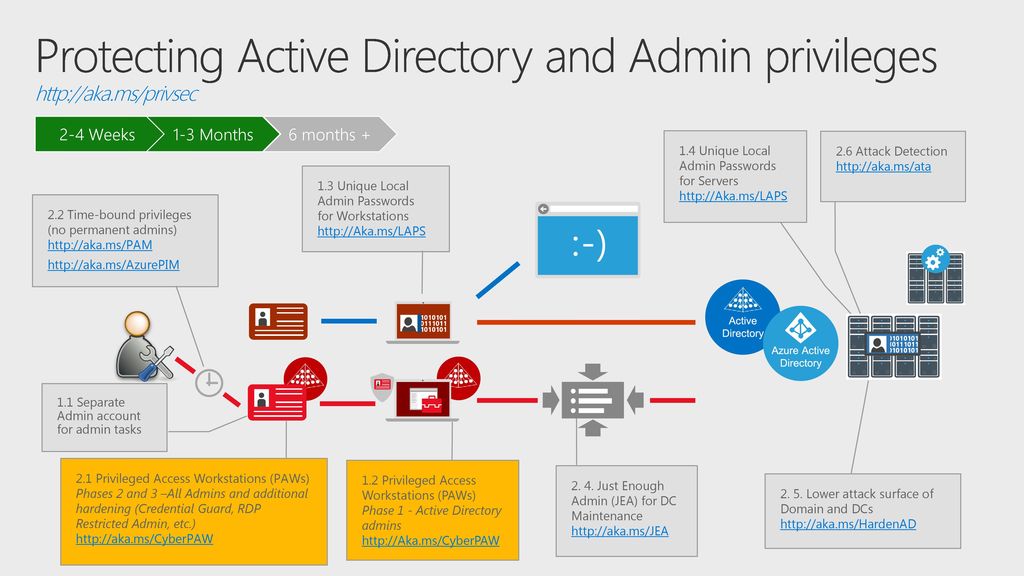
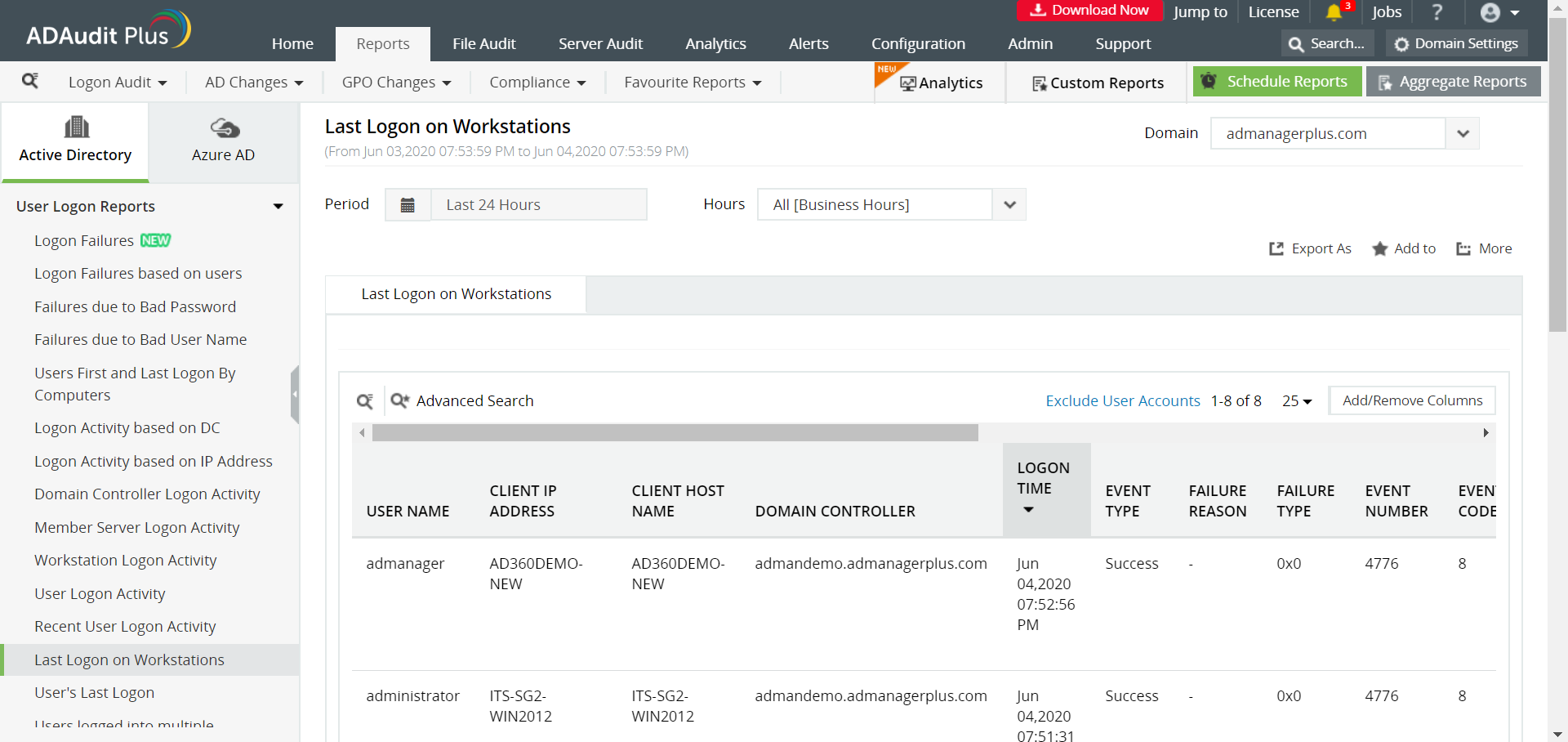
5/31/2018 3:40 PM BRK3113 How Microsoft IT builds Privileged Access Workstation using Windows 10 and Windows Server 2016 Jian (Jane) Yan Sr. Program Manager. - ppt download