
Managing AWS Account Root MFA Using CyberArk Privileged Access Manager | AWS Partner Network (APN) Blog

Just-in-Time Least Privileged Access to AWS Administrative Roles with Okta and AWS Identity Center | AWS Partner Network (APN) Blog

How to centralize and automate IAM policy creation in sandbox, development, and test environments | AWS Security Blog

CyberArk Launches Identity Security Platform Shared Services with Support from AWS SaaS Factory | AWS Partner Network (APN) Blog

Open sesame: Granting privileged access to EC2 instances with Session Manager | AWS Cloud Operations & Migrations Blog

Open sesame: Granting privileged access to EC2 instances with Session Manager | AWS Cloud Operations & Migrations Blog

IAM makes it easier for you to manage permissions for AWS services accessing your resources | AWS Security Blog

Continuous permissions rightsizing to ensure least privileges in AWS using CloudKnox and AWS Config | AWS Cloud Operations & Migrations Blog
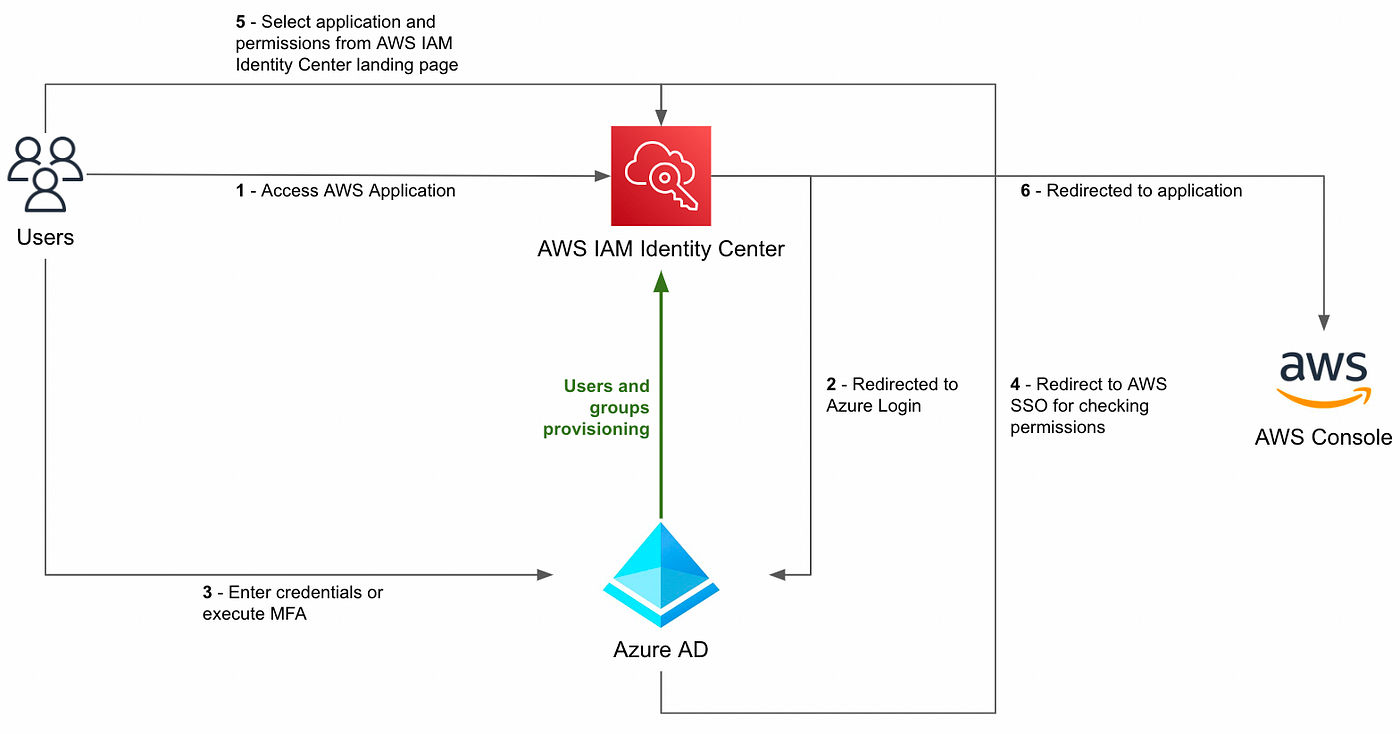
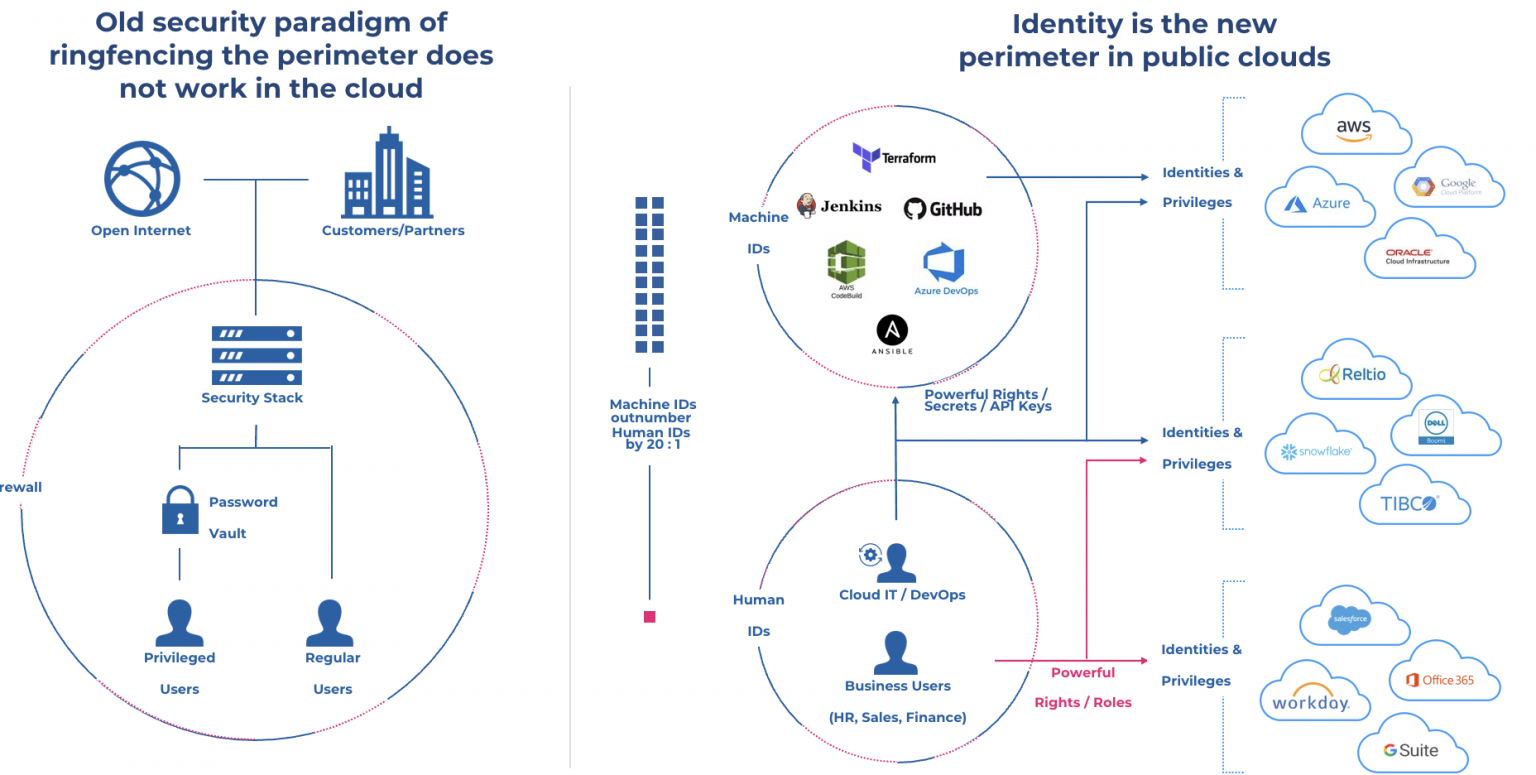









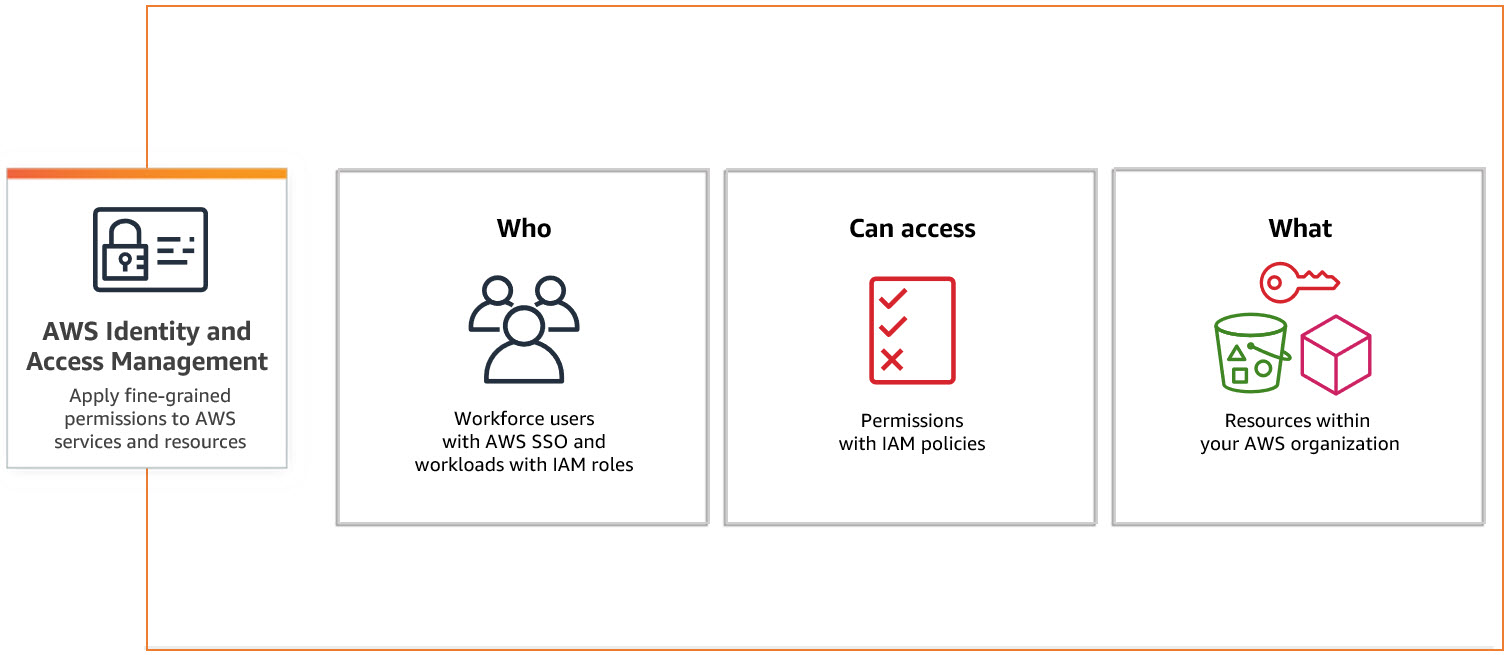

VPC.png)
