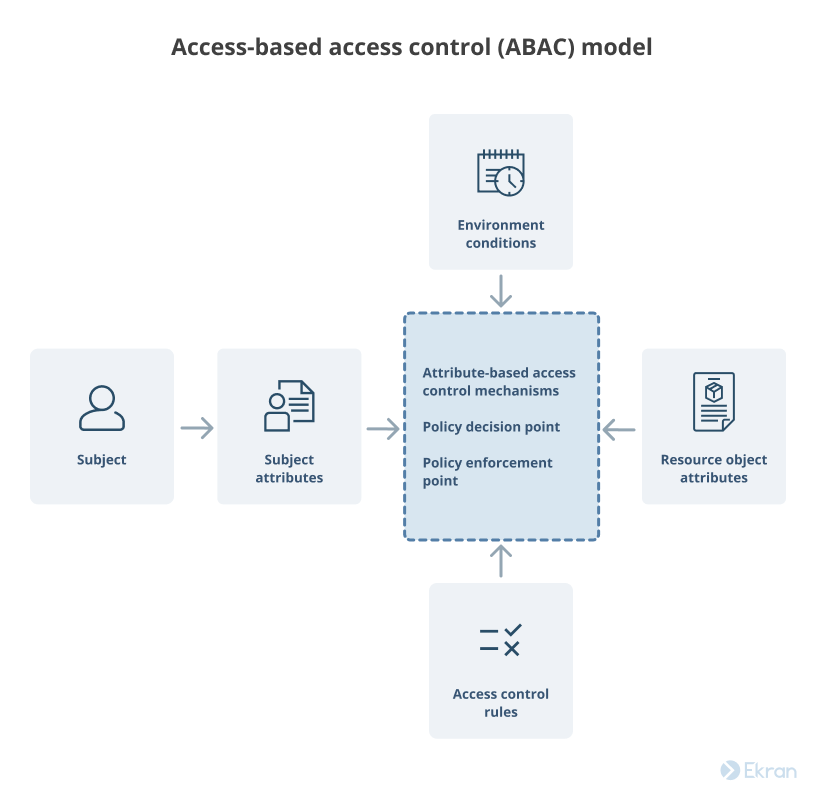
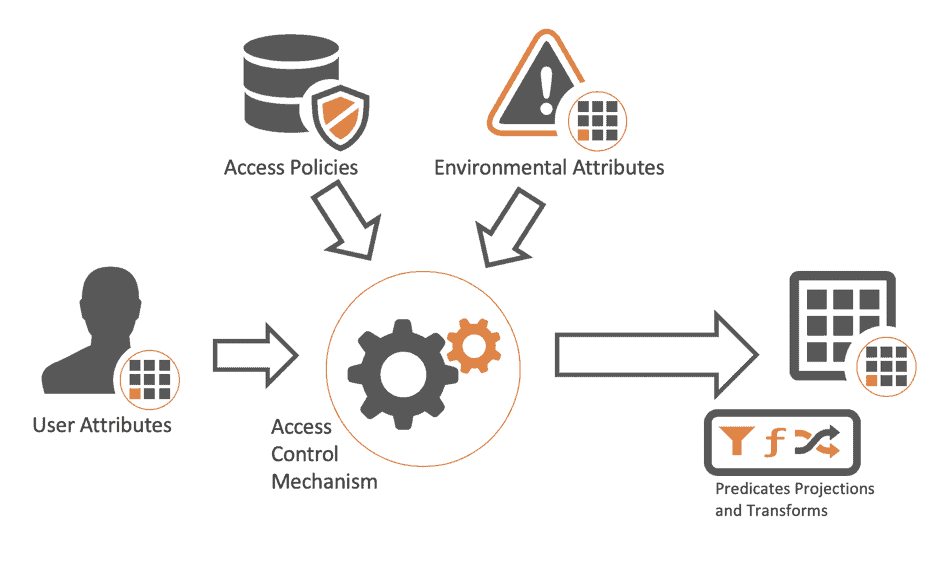
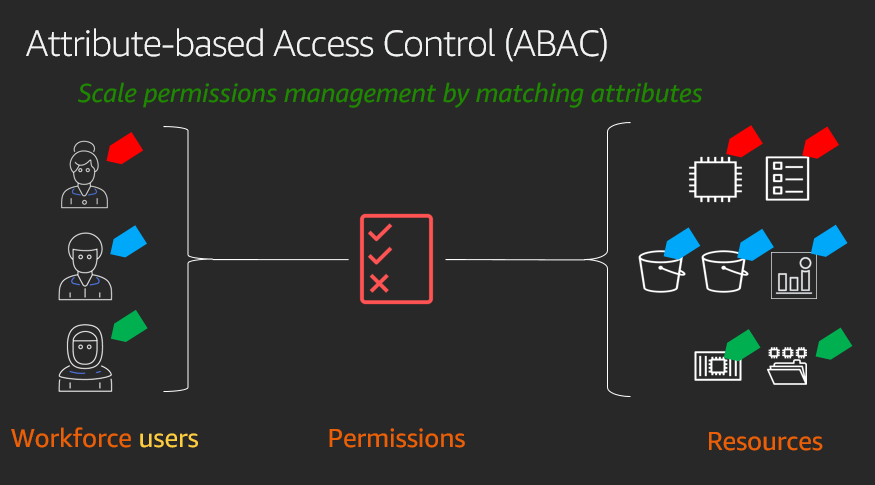
Attribute-based Access Control (ABAC) and a DDD application - Questions / Help - Elixir Programming Language Forum

Figure 2 from Comparison of Attribute Based Access Control (ABAC) Model and Rule Based Access (RBAC) to Digital Evidence Storage (DES) | Semantic Scholar
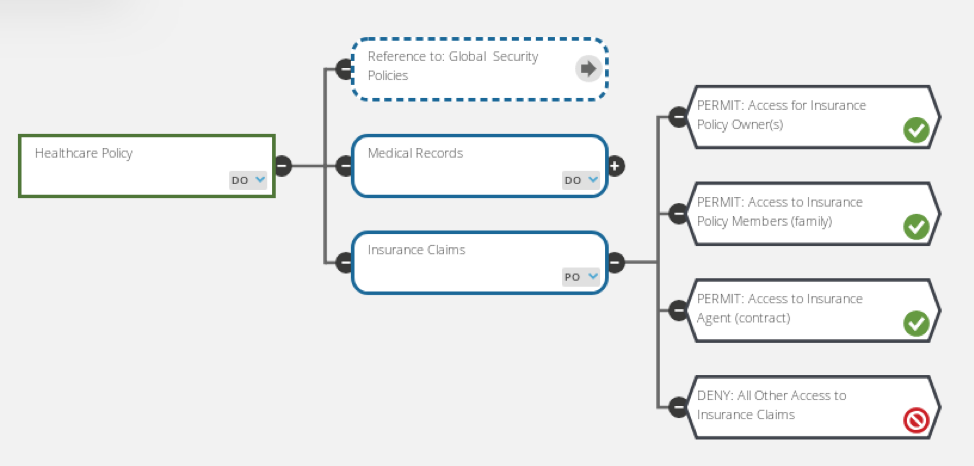
DZone: Why Attribute-Based Access Control - The Evolution from RBAC to ABAC in Data Access Control - Axiomatics